TL;DR:
- SSH login to QNAP
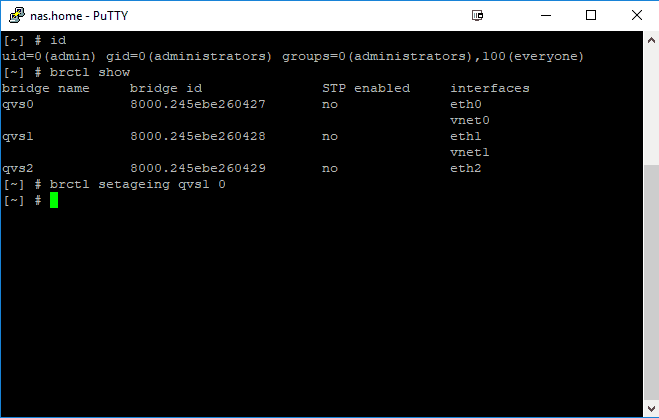
- Identify virtual switch you want to put into monitoring mode, in my case qvs1
- Set ageing to 0
brctl show brctl setageing qvs1 0
My example:
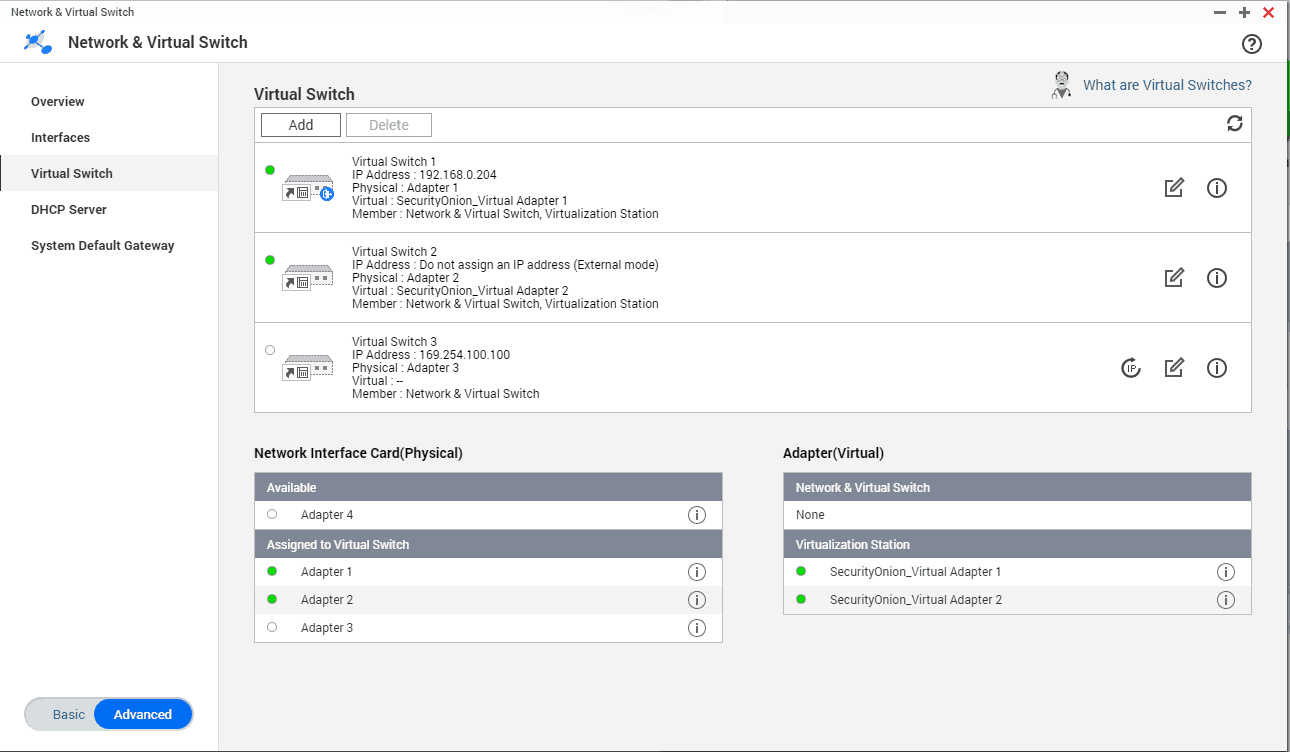
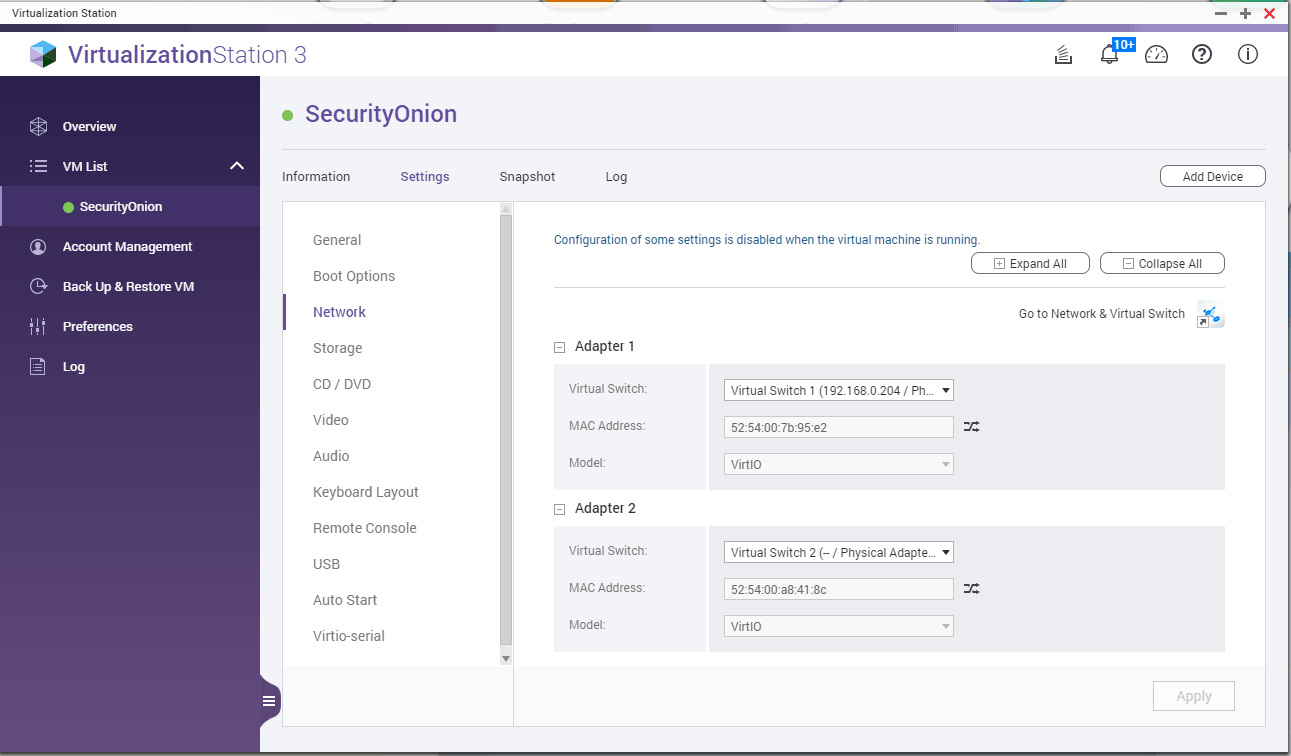
I’ve created a virtual machine (SecurityOnion) on my QNAP virtualization station to monitor my home network traffic. I have setup a port mirroring on my switch to send all traffic to the QNAP ethernet adapter number 2. (My QNAP has 4 ethernet adapters). Sniffing OS usually needs two ethernet adapters, one for management and one dedicated for monitoring (sniffing). I’ve created a new virtual switch in QNAP with adapter number 2 and set it to external mode (no IP address), then I assigned this virtual switch to monitoring interface in SecurityOnion. I should’ve been able to see all the traffic now, but that wasn’t the case. There were no packets flowing to my monitoring ethernet adapter. After some investigating I found out a reddit user had the same problem. This is the solution:
SSH into your QNAP with your admin username and credentials. Check your virtual switches with a command “brctl show“, this will list all virtual switches you created. Now you need to select the virtual switch you assigned to your sniffing ethernet adapter in my case, that was adapter number 2 and run the following command: “brctl setageing qvs1 0″, where qvs1 is the number of your selected virtual switch (one that will do the sniffing, in my case adapter 2, identified as qvs1). That’s it, you should see all packets on the sniffing interface now. Thanks go to the reddit user I don’t want to name due privacy concerns.
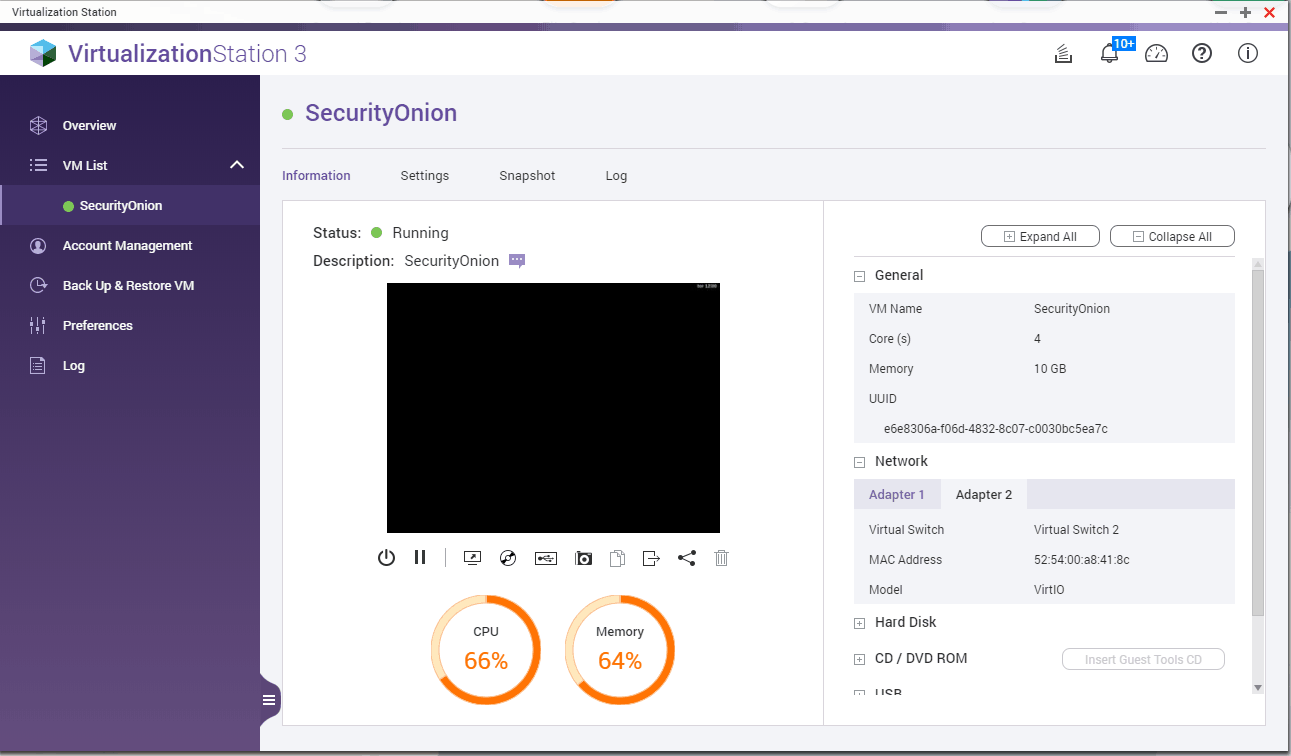
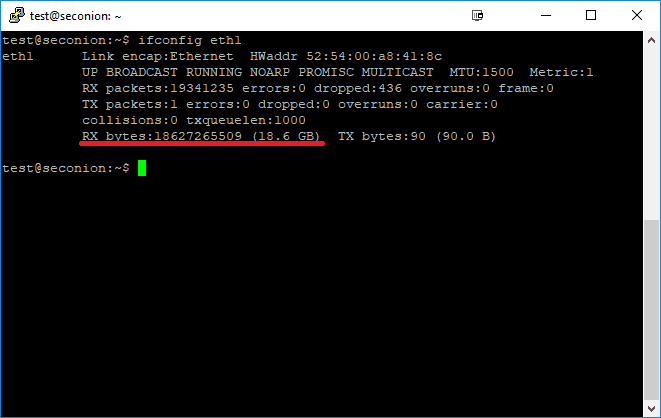
SecuritOnion is now receiving packets on the monitoring interface:
Side note: Sniffing and analyzing traffic is heavy on CPU, HDD and RAM resources. Qnap is not a suitable candidate for that. My Qnap tests showed a CPU bottleneck (quad core celeron N3160) averaging around 70% cpu usage with low network traffic and less than 20 devices on the network.
Hi,
Thanks for sharing this article; I was exactly looking for this.
I’m always cautious making changes without a back out plan.
Do you know how we can back out from this command?
Just set it back to default. I think default ageing time is 300.
brctl setageing qvs1 300
Thank you for this, it is extremely useful. Does this configuration survive reboot ?
Have you done this on QuTS hero at all? I’m testing it now but doesn’t seem to be working.
Hey,
this was done in the year 2018. I haven’t tested the newest firmware.