TL;DR:
Xerox phaser 3020 black ink percentage remaining – SNMP cacti data and graph template at the bottom of this post.
With some tweaks this method should also works for other brand printers.
With the help of this article: https://thwack.solarwinds.com/docs/DOC-171511 I could set up a cacti template for my Xerox 3020 printer. Some printers return ink level value in percents but in my case I got only the raw value.
1. Get SNMP toner max capacity value, OID for that is 1.3.6.1.2.1.43.11.1.1.8.1.1
root@cacti: snmpget -v2c -c public 192.168.0.251 1.3.6.1.2.1.43.11.1.1.8.1.1
SNMPv2-SMI::mib-2.43.11.1.1.8.1.1 = INTEGER: 700
700 is the raw value for 100% toner capacity.
2. Get SNMP toner current levels value, OID for that is 1.3.6.1.2.1.43.11.1.1.9.1.1
root@cacti: snmpget -v2c -c public 192.168.0.251 1.3.6.1.2.1.43.11.1.1.9.1.1
SNMPv2-SMI::mib-2.43.11.1.1.9.1.1 = INTEGER: 686
686 is the current raw value of my toner levels. To calculate toner ink percentage remaining we need to divide current raw value (686) with max raw value (700) and multiply it by 100. 686 / 700 * 100 = 98 (percentage of ink remaining). Since the max raw value is a nice number (700), we can just divide current raw value with 7, 686/7 = 98. We can use this formula for our CDEF definitions in cacti later. Remember, this is only for Xerox 3020, other brand printers can output different raw values and you need to correct this formula accordingly.
Xerox 3020 ink remaining percentage formula: raw_current_ink_level / 7
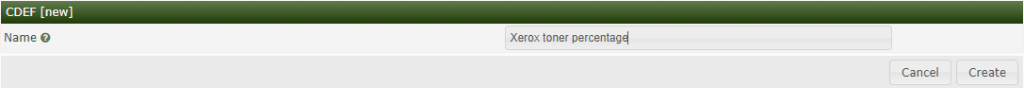
3. Login to cacti and go to Console -> Presets -> CDEFs
Click plus sign and create new CDEF and name it Xerox toner percentage
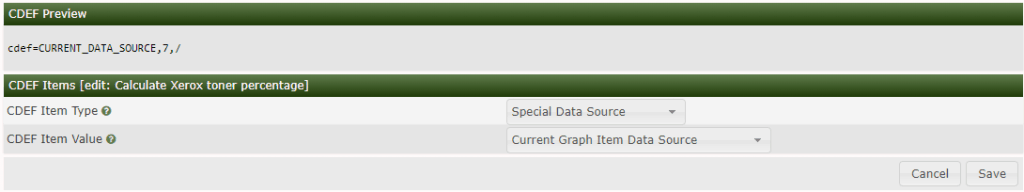
Click plus at CDEF Items.
CDEF Item Type: Special Data Source
CDEF Item Value: Current Graph Item Data Source
Click Save
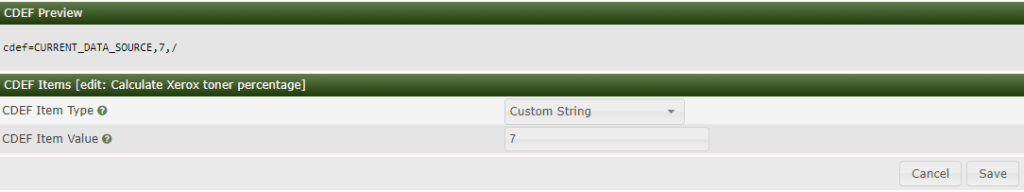
Click plus at CDEF Items.
CDEF Item Type: Custom String
CDEF Item Value: 7 (this is the value cacti will use to divide raw data)
Click Save
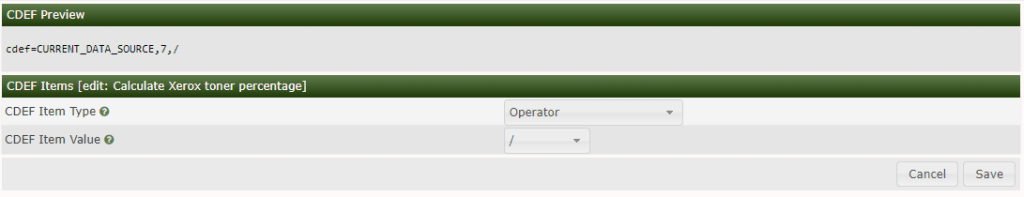
Click plus at CDEF Items.
CDEF Item Type: Operator
CDEF Item Value: / (this will tell cacti to use a divide operation with the custom string we defined in a previous step).
Click Save
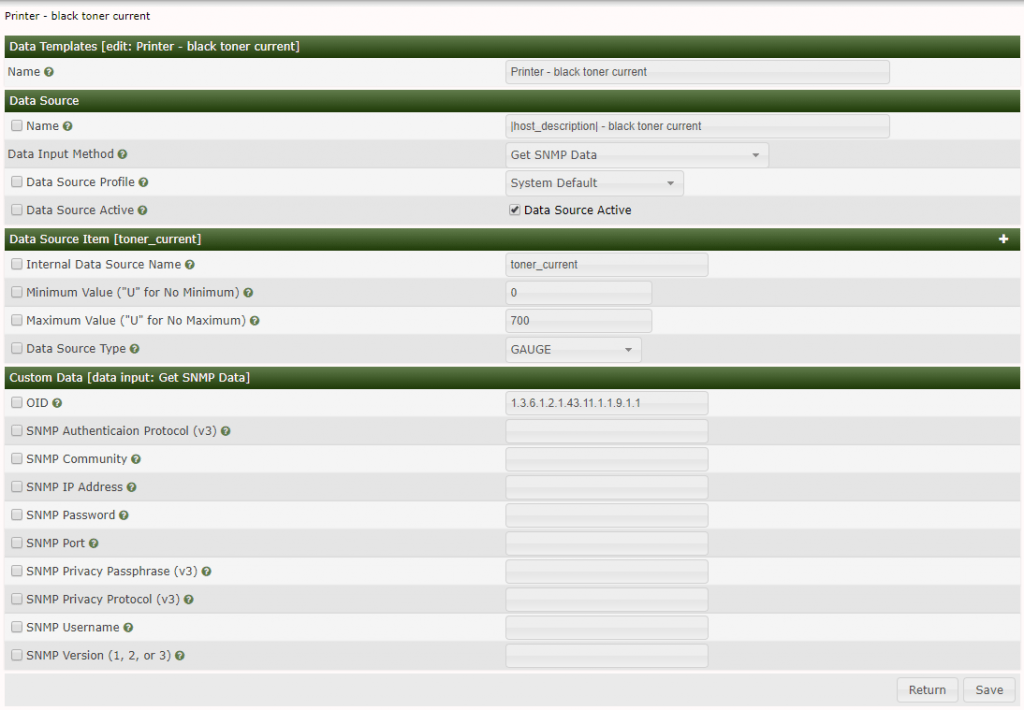
4. Go to Console -> Templates -> Data Source
Click plus to create new data source template and name it Printer – black toner current
Name: |host_description| – black toner current
Data Input Method: Get SNMP Data
Data Source Active: tick the right box
Internal Data Source Name: toner_current
Click Create
New Custom Data field will appear.
OID: 1.3.6.1.2.1.43.11.1.1.9.1.1
Click Save
5.1 Go to Console -> Templates -> Graph
Click plus sign
Name: Printer – black toner levels
Title: Printer – black toner levels
Vertical Label: percent
Tick Rigid Boundaries Mode
Upper Limit: 100
Click Create
5.2 Now click plus sign at Graph Template Items
Graph Item Type: AREA
Data Source: Printer – black toner current
Color: select what you like
Consolidation Function: AVERAGE
CDEF Function: Xerox toner percentage
Text Format: Available
Click save
Add another Graph template item
Graph Item Type: GPRINT
Data Source: Printer – black toner current
Consolidation Function: LAST
CDEF Function: Xerox toner percentage
GPRINT Type: Percent(Round down to the nearest decimal)
Text format: Current:
Click Save
Add another Graph template item
Graph Item Type: LINE1
Data Source: Printer – black toner current
Consolidation function: AVERAGE
CDEF function: Xeror toner percentage
Save
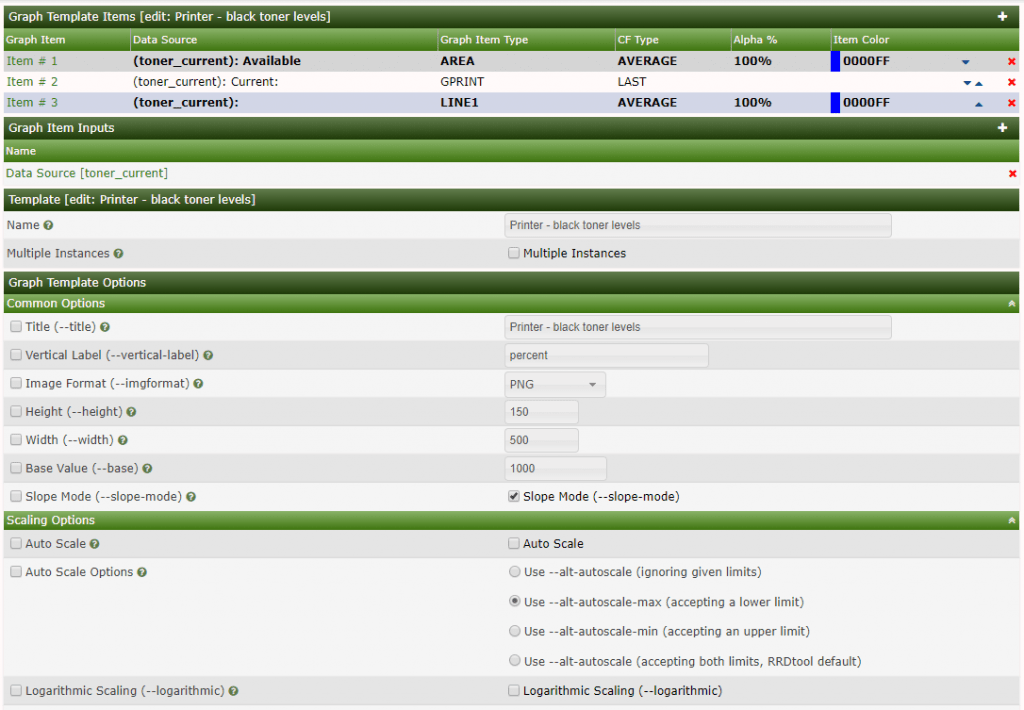
Your graph is now ready to device assignment.
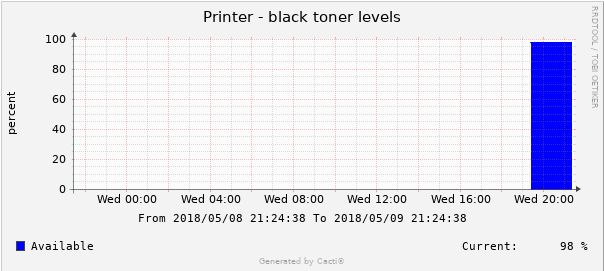
Final result:
Download data and graph templates for xerox phaser 3020:
xerox_3020_cacti_toner_level_template