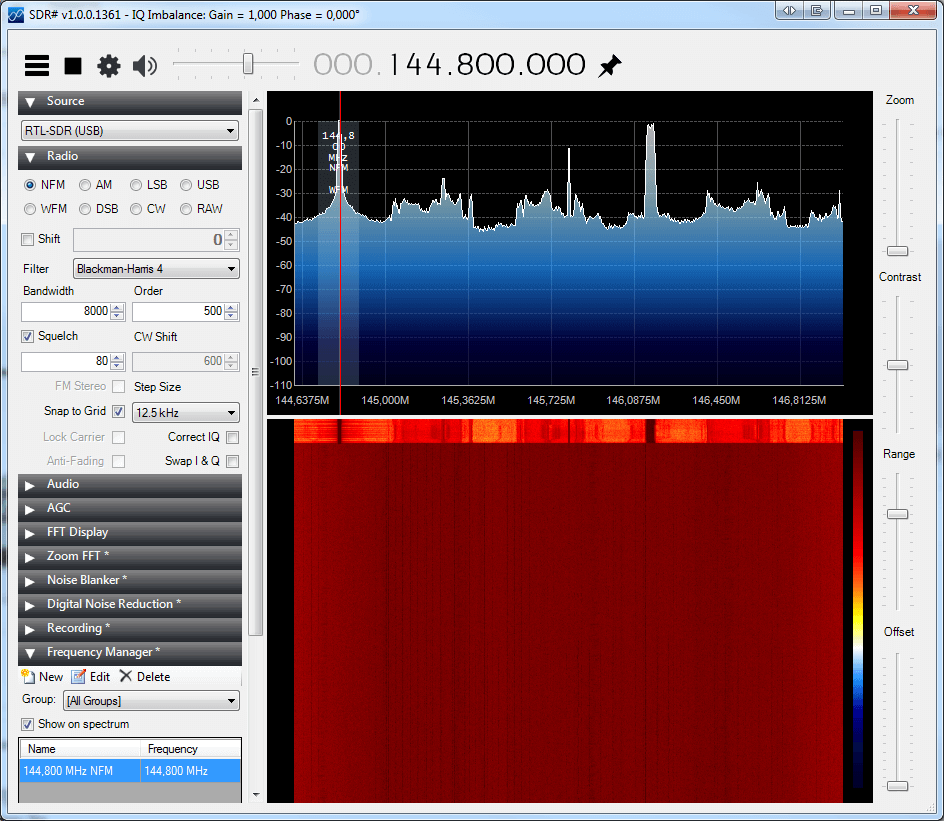
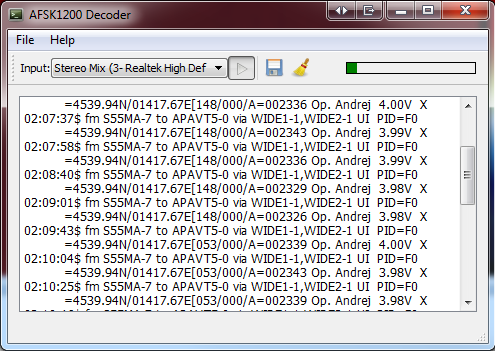
I used my RaspberryPI to setup an APRS digipeater. The software I used is called Xastir. The problem is, there are no good default maps to use in Xastir.
This tutorial will guide you how to install OSM maps into Xastir software. Maps are generated on a Windows machine, then transferred to a Linux machine where Xastir is running.
TL;DR version:
1. Download Taho application for Windows.
2. Select area, copy bbox text.
3. Paste bbox text to Taho, click on bbox button, select parameters and click on make maps.
4. Upload generated .inf and .jpg files to your Xastir map folder.
5. Download inf2geo.pl to your linux machine and convert .inf files to .geo files.
6. Start or restart Xastir, select your map and apply.
Detailed version:
1. Download Taho application for Windows (Version 4.01 didn’t work on my PC, you should download older versions, if you can’t run the newest version).
2. When you launch the Taho application, it will also open the bbox tool site.
3. On the bbox tool site, center map to your desired location and click button “select area”. Select your area.
Note: If you select too big area, you won’t be able too select top zoom levels in the next steps.
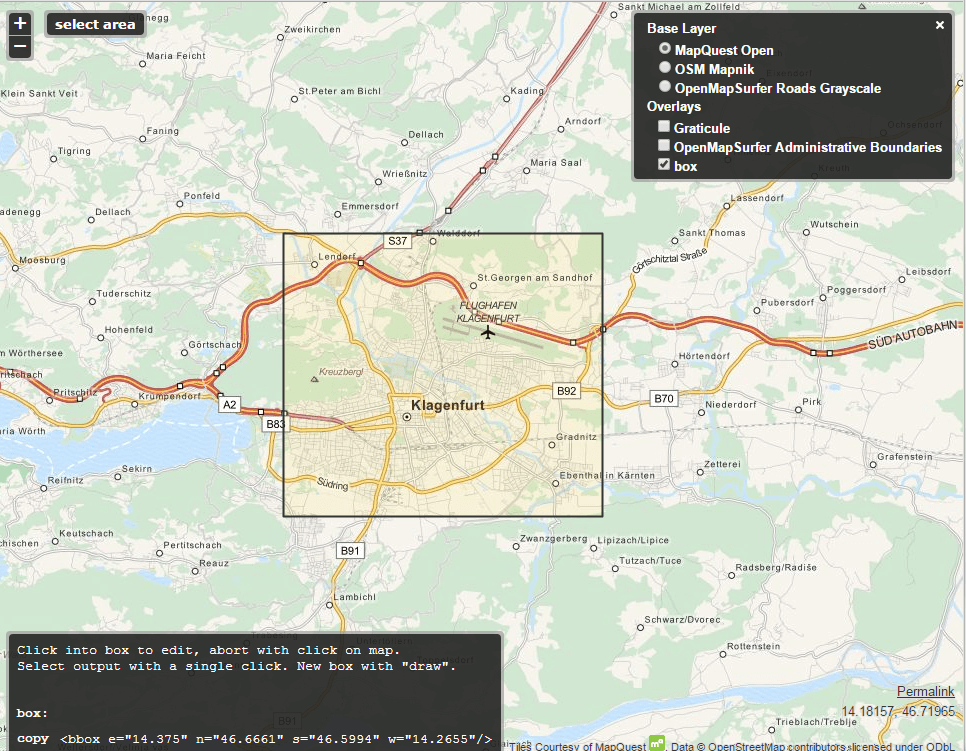
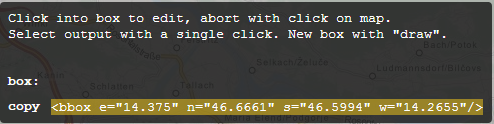
4. Copy code in the grey box to your clipboard.
5. Open Taho application and paste the code into “Get from <bbox…>” field. Click on the bbox button now. It should populate coordinates into Taho application. Select UI-View in Kal.-Files, .jpg for file type, zoom level (16 is good for small city), size (should be free, whole area in 1 file), define path for saving your maps and click on make maps button.
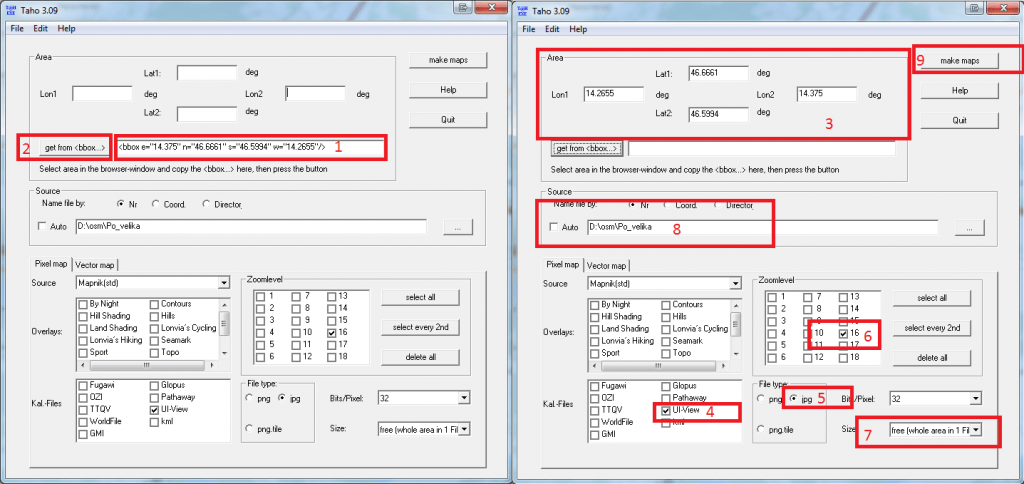
6. Each selected zoom level generates separate .jpg and .inf files in your defined maps path (step above).
7. Xastir doesn’t know how to handle .inf files so we need to convert them to .geo format. Upload your .jpg and .inf files to Xastir map folder. In my case, maps are located in /usr/share/xastir/maps Fire up your linux console and
Download inf2geo.pl converter and convert .inf files:
sudo cd /usr/share/xastir/scripts
sudo wget https://raw.githubusercontent.com/mgrennan/xastir/master/scripts/inf2geo.pl
sudo chmod +x inf2geo.pl
sudo ./inf2geo.pl /usr/share/xastir/maps/yourmap.inf
By now, you should have yourmap.geo file in /usr/share/xastir/maps
Open .geo file with your favourite editor and correct the path if you have to.
FILENAME maps/yourmap.jpg
TIEPOINT 0 0 16.0645 45.8288333333333
TIEPOINT 5631 5887 14.661666666667 46.8525
IMAGESIZE 5632 5888
#5632x5888
#
# Converted from a .INF file by WE7U's inf2geo.pl script
#
Note: If you change the name of the file, you also have to change FILENAME in yourmap.geo accordingly.
8. Start or restart Xastir, go to Map -> Map Chooser -> select your map -> Apply -> profit.